PHP applications are vulnerable due to several factors. Firstly, PHP's flexibility often leads to loosely written code where input validation and output might be overlooked. Developers, especially beginners, might inadvertently create security holes by not handling user inputs properly. Secondly, PHP's open-source nature means extensive documentation and community support, but it also means that vulnerabilities and their fixes are widely known, making it a prime target for attackers. Thirdly, the wide array of extensions and libraries available might not always be secure, leading to unintended vulnerabilities if not used cautiously. Lastly, the decentralized nature of PHP development can result in inconsistencies in coding practices, potentially leading to vulnerabilities if best practices are not followed consistently across all parts of an application.
In essence, PHP as a server-side language has 76.8% of websites in 2023 as per W3Techs. Its ease of use led to its growing usage; however, it also led to vulnerabilities. With proper coding practices, awareness, and regular updates, developers can mitigate these risks and create robust and secure PHP applications.
Secure Your PHP Applications from Common Vulnerabilities
1. Cross-Site Scripting (XSS)
How it works: Hackers insert harmful code into web pages that users view, allowing them to steal important information or control the user's actions without permission.
How to fix: Sanitize user input and escape output. Use htmlspecialchars() to encode special characters.
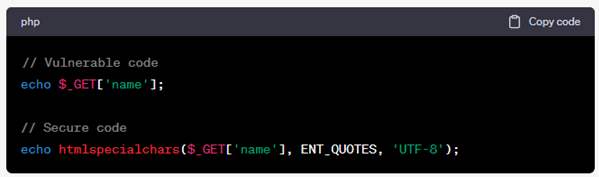
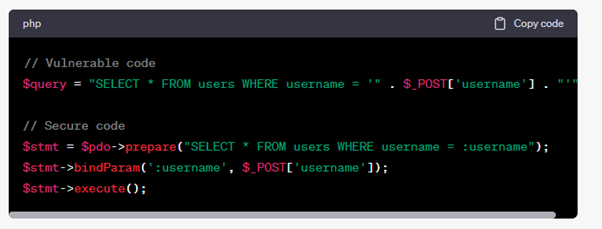
2. SQL Injection
How it works: Hackers input harmful SQL code, potentially exposing or destroying your database.
How to fix: Use prepared statements and parameterized queries to separate SQL code from user data.
Example:
3. Cross-Site Request Forgery (CSRF)
How it works: Hackers compel users into accomplishing actions without their consent by exploiting their session.
How to fix: Use anti-CSRF tokens to validate the origin of requests.
Example:
-jpg.jpeg)
4. Remote Code Execution (RCE)
How it works: Attackers perform arbitrary code on the server, achieving control over the application.
How to fix: Avoid dynamic evaluation of user input and update PHP to the latest version.
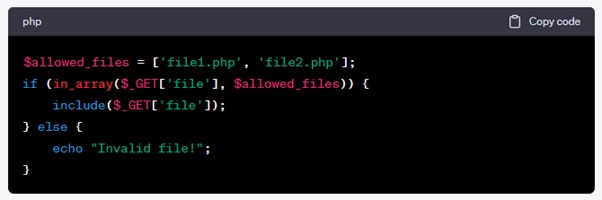
5. File Inclusion Vulnerabilities
How it works: Attackers include files from external sources, potentially exposing sensitive data or executing malicious code.
How to fix: Avoid user-controlled data in include statements. Use a predefined list of allowed files.
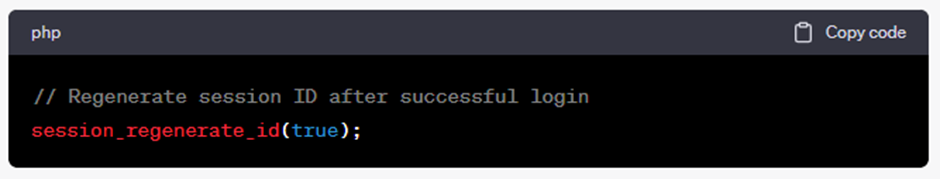
6. Session Hijacking
How it works: Attackers steal session identifiers, impersonating users.
How to fix: Use secure, HttpOnly, and SameSite attributes for cookies. Regenerate session IDs after login.
Example:
7. Insecure Direct Object References (IDOR)
How it works: Attackers manipulate input to access unauthorized data.
How to fix: Implement proper authentication and permission. Avoid exposing internal implementation details.
8. Invalidated File Uploads
How it works: Attackers upload malicious files, compromising the server's integrity.
How to fix: Validate file types, restrict file permissions, and store files outside the web root directory. Check file types using mime_content_type().
9. Insecure Cryptography
How it works: Weak encryption algorithms or poor key management practices compromise data security.
How to fix: Use strong encryption algorithms and secure key management. Avoid outdated and weak encryption methods.
10. Code Injection
How it works: Attackers inject code into functions that perform code execution.
How to fix: Avoid using user input in functions like eval(). If dynamic code execution is necessary, sanitize and validate user input rigorously.
11.The Role of REST API with PHP
How It Works: REST API with PHP ensures secure communication by validating inputs, utilizing OAuth for access control, and implementing HTTPS encryption for data transmission.
How to Fix Security Issues: Enhance security with strict input validation, output sanitization, and OAuth authentication. Implement HTTPS for encrypted data transfer and conduct regular security audits to identify and fix vulnerabilities.
Example: In an e-commerce app, PHP validates inputs, OAuth ensures secure access, and HTTPS encrypts payment data. Continuous updates and security checks maintain application resilienceo vulnerabilities if best practices are not followed consistently across all parts of an application.
Essential Skills for PHP Developers: Ensuring Application Security
Securing PHP applications requires PHP developers to possess a diverse skill set beyond just programming expertise. Important skills needed to ensure the security of applications:
- Deep Understanding of Web Security Concepts: Familiarity with XSS, SQL injection, CSRF, etc.
- Knowledge of PHP Security Best Practices: Including input validation, output sanitization, and secure file handling.
- Awareness of Security Libraries and Tools: Such as OWASP PHP Security Project and security scanners.
- Experience with Secure Coding: Avoiding insecure functions and writing secure code.
- Understanding of Cryptography: Knowledge of encryption algorithms and secure hashing.
- Ability to Implement Authentication and Authorization: Making strong systems to confirm users and permit their actions securely.
- Familiarity with PHP Framework Security Features: Utilizing security features provided by frameworks like Laravel and Symfony.
- Regular Updating and Patching: Keeping PHP and related libraries updated with security patches.
- Problem-solving skills: Capacity to find and resolve security-related issues efficiently.
- Effective Communication and Collaboration: Working collaboratively and communicating security concerns effectively within the team and with stakeholders.
By considering these vulnerabilities and executing the suggested fixes, you can secure PHP applications. Regularly update your PHP version and dependencies, stay informed about the latest security threats, and employ a robust firewall and intrusion detection system for added protection. Stay vigilant, and your PHP applications will be much more resistant to cyber threats.
If you seek experienced and skilled professionals, hire PHP developers for expertise in PHP development. Trust our team to elevate your web applications with our unparalleled PHP development services.
































